General Information
Executive Summary
Microsoft is aware of limited, targeted attacks that attempt to exploit a vulnerability in Internet Explorer 6, Internet Explorer 7, Internet Explorer 8, Internet Explorer 9, Internet Explorer 10, and Internet Explorer 11.
The vulnerability is a remote code execution vulnerability. The vulnerability exists in the way that Internet Explorer accesses an object in memory that has been deleted or has not been properly allocated. The vulnerability may corrupt memory in a way that could allow an attacker to execute arbitrary code in the context of the current user within Internet Explorer. An attacker could host a specially crafted website that is designed to exploit this vulnerability through Internet Explorer and then convince a user to view the website.
On completion of this investigation, Microsoft will take the appropriate action to protect our customers, which may include providing a solution through our monthly security update release process, or an out-of-cycle security update, depending on customer needs.
We are actively working with partners in our Microsoft Active Protections Program (MAPP) to provide information that they can use to provide broader protections to customers. For information about protections released by MAPP partners, see MAPP Partners with Updated Protections.
Microsoft continues to encourage customers to follow the guidance in the Microsoft Safety & Security Center of enabling a firewall, applying all software updates, and installing antimalware software.
Mitigating Factors:
-
By default, Internet Explorer on Windows Server 2003, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, and Windows Server 2012 R2 runs in a restricted mode that is known as Enhanced Security Configuration. This mode mitigates this vulnerability.
-
By default, all supported versions of Microsoft Outlook, Microsoft Outlook Express, and Windows Mail open HTML email messages in the Restricted sites zone. The Restricted sites zone, which disables script and ActiveX controls, helps reduce the risk of an attacker being able to use this vulnerability to execute malicious code. If a user clicks a link in an email message, the user could still be vulnerable to exploitation of this vulnerability through the web-based attack scenario.
-
An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
-
In a web-based attack scenario, an attacker could host a website that contains a webpage that is used to exploit this vulnerability. In addition, compromised websites and websites that accept or host user-provided content or advertisements could contain specially crafted content that could exploit this vulnerability. In all cases, however, an attacker would have no way to force users to visit these websites. Instead, an attacker would have to convince users to visit the website, typically by getting them to click a link in an email message or Instant Messenger message that takes users to the attacker’s website.
More information in the full article. There is no patch. But Microsoft has given some recommendations which are easier to understand at Security Garden’s posting:
Recommendations
As illustrated in the “Security Research and Defense Blog” reference below, users of IE 10 and 11 should ensure they haven’t disabled Enhanced Protection Mode.
Another option is to install the Enhanced Mitigation Experience Toolkit (EMET). The recommended setting for EMET 4.1, available from KB Article 2458544, is automatically configured to help protect Internet Explorer. No additional steps are required.
See the Tech Net Advisory for instructions on changing the following settings to help protect against exploitation of this vulnerability:
-
Change your settings for the Internet security zone to high to block ActiveX controls and Active Scripting
-
Change your settings to prompt before running Active Scripting or to disable Active Scripting in the Internet and Local intranet security zone.
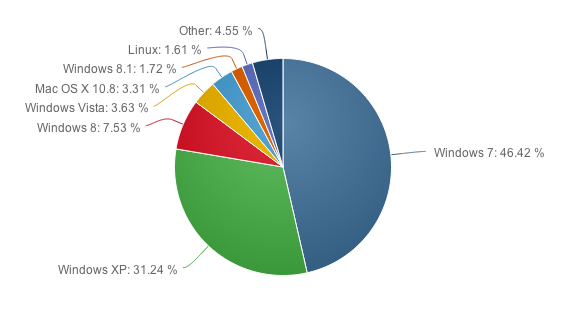
Those still using Windows XP on the Internet, please be aware:
VERY IMPORTANT FOR ANY HOLD OUT WINDOWS XP USERS
This is the first of the security vulnerabilities that DOES NOT include workarounds for Windows XP. The oldest Windows noted as being affected are: Windows Server 2003 SP2 and Vista SP2.
IMPORTANT NOTE: Once a Microsoft product’s support has expired — as is true now about Windows XP SP3 since April 8, 2014 — Microsoft no longer lists it as affected by the vulnerabilities being patched. Microsoft only list Windows versions which are still under Mainstream Support or Extended Support. This has always been the case.
If anyone is still using Windows XP on the Internet (UNWISE!!), it would be strongly recommended to disallow IE (Internet Explorer) access to the Internet through your software firewall*, and use another browser like Firefox and Google Chrome which will still be getting updates for a time.
* Any Windows XP users still on the Internet should at least have:
- a hardware router with Stateful Packet Firewall
- should be using a ‘real’ software firewall as well as a good AV program. Just one good choice that will continue to support Windows XP is ESET’s Smart Security which is a very good antivirus and firewall. It is the one I use. It is not free. There are several free antivirus programs but not many free security suites.
- block Internet Explorer through the ESET or other software firewall.
- should be using a 3rd party browser like Mozilla Firefox with NoScript, Adblock Plus and WOT to help sort out safer search results on search engines, or Google Chrome with ScriptSafe, Adblock Plus and WOT Extension.
- uninstall Java entirely, keep Adobe Flash religiously updated for Firefox as long as Adobe continues to provide them. Google Chrome updates Flash within itself. Might want to switch from Adobe Reader to Sumatra PDF reader which is a simple PDF viewer.
- need to be even more careful than ever before about where you go. The bad guys will be looking with great anticipation for computers with expired Windows XP.
- no risky behavior
- no banking … note very soon banks will be disallowing expired Windows XP entirely anyway.
IMPORTANT: You can not block a program from getting out to the Internet with the Windows XP Firewall. It is only a one way firewall. It only monitors incoming Internet requests, instead of both ways as any real firewall including Windows 7 and Windows 8 built-in software firewalls do.
Here’s a quote from a ZDNet article:
To those planning to stick resolutely with the aged Windows XP operating system even after Microsoft ends support next year, the advice from experts is simple: Don’t do it.
Again: I would strongly suggest you get a new computer, upgrade your computer if it can be upgraded to a modern/still supported Windows such as Windows 7 or Windows 8, or get a Mac, or you could convert/upgrade the computer to Linux or use a Linux LiveCD to visit the Internet and still use Windows XP as a standalone NOT CONNECTED TO THE INTERNET computer.
If you need help with any of this, please contact your computer guru, join a forums like Scot’s Newsletter Forums – BATL (Bruno’s All Things Linux) to ask questions, or you can use the contact info on my website to contact me for some help.








You must be logged in to post a comment.