Windows XP has been around since August 24, 2001 – 12 years ago now. It is getting VERY long in the tooth.
Windows XP SP3 and Office 2003 Support Ends April 8th, 2014
Like many Operating System versions, Windows XP was not such a great OS in the beginning. BUT, like many Microsoft products, it got better after Service Pack 1 (SP1), but wasn’t the best it could be till after Service Pack 2 (SP2) and mildly better after Service Pack 3 (SP3). SP3 is the current version of Windows XP.
I loved Windows XP for a long time, even though it was getting long in the tooth. But I have come to love Windows 7 even more. Windows 8 … the jury is still out. For me I use several different operating systems. I also love and use Mac OS X or just OS X (as it is called now) and Debian Linux.
Windows XP has been on life support or Extended Support since April 8, 2009 when Mainstream Support ended. That was after two says of execution as it were since it was supposed to be ended earlier than 2009.
Windows XP has been the main stay for many folks for a long time in the Windows world — the last 12 years. That’s a long time for an Operating System version.
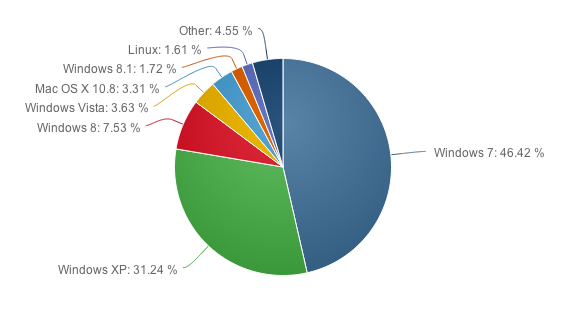
Windows XP still holds the #2 spot at 31.24% of computer users as shown below in the graph from NetMarketShare.com:
Windows 7 holds the #1 spot for a very good reason. It is still the best of the newer Operating Systems from Microsoft to date — in my opinion and nearly half of all Windows users to date. And Windows 7 is still good to go until January 14, 2020 (end of Extended Support – it is still in Mainstream Support until January 15, 2015). Here’s the break out of the Windows lifecycle fact sheet info:
I have said all this because we need to see where were are, and where we need to be as computer users, particularly as Windows users with April 8, 2014 looming over those of us still using Windows XP.
Especially in the light of the pervasive malware purveyors out there today.
We need to make sure we are all no longer using Windows XP of any kind before or at least by April 8, 2014 when Microsoft will no longer be providing ANY security updates for Windows XP.
A few years back they did the same thing with Windows 2000. It’s now Windows XP’s turn.
Please read the following articles to see why this will be very important:
Windows XP infection rate may jump 66% after patches end in April – Computerworld
Microsoft yesterday again put the scare into Windows XP users, telling them that after April 8, 2014, the chance that malware will infect their PCs could jump by two-thirds.
Windows lifecycle fact sheet – Microsoft.com (image above)
New stats show Windows 8 usage up sharply as XP usage plummets – ZDNet (for curiosity though, look at the difference between the table on ZDNet’s article and the one today).
NetMarketShare (choose Operating Systems from the dropdown to see the chart above in real time)
It would appear, that, as predicted, many around the world are moving to other types of computers, in particular mobile devices. This was forecast and it would seem to be coming to pass rather dramatically now.
It is amazing to see the number of people who rarely if ever use their desktop computers these days, relying on their mobile devices for almost all, if not all, their computing and Internet needs. Some folks no longer even have a computer other than a tablet, like the iPad or Nexus Tablet, or Surface, etc., or just use their smartphones for their email, browsing, messaging, gaming, etc. which is the bulk of what people seem to do on the Internet these days. Unless of course if their work or business, or gaming bents, are important to them. Having said that, even gaming has very much gone mobile for many people.
I am hoping that folks will take a look at the overall picture and determine which direction they wish to go now that there are only a few months left before Windows XP will no longer be a viable Internet connected computer.
Will a Desktop or Laptop be the way to go, or will a Mobile device like a Tablet or maybe even just a smartphone be enough for many folks? Staying with Windows or moving to a Mac may also be a consideration.
No matter which way folks ultimately go, deciding will be important and thinking about this is really needed with Windows XP going away in just a short few months.
Over 31% of computer users will need to make this decision before April 8, 2014, if they wish to remain as safe as they can be on the Internet.
Even with Google Chrome continuing to support Windows XP SP3 a year after Microsoft (till 2015), if the Operating System itself has no updates, that will certainly not be enough.
Lots to think about and only a few months to decide … Windows XP SP3 and Office 2003 Support Ends April 8th, 2014




You must be logged in to post a comment.